Abstract
In today's article I will review how to build a minimal virtualized mainframe. This will be hosted on our lab xen cluster, in an ubuntu vm via hercules.
High level objectives:
- Build ubuntu host
- Install pre-reqs for mvs38 tur(n)key 4
- Smoke test the system
- Lessons learned
Build ubuntu host
This objective will be pretty straight forward. Ideally I would deploy a configuration mangaged template... since we are still lazy hackers... I will build it from scratch, and climb the configuration management hill another day.
I will let you figure out how you want yours built. I went with a "mostly accept the defaults" approach for this example system.
Install pre-reqs for mvs38 tur(n)key 4:
- A tn3270 emulator
- I will use c3270... because it's a tui
- The virtualization environment
- It's hercules under everthing, but it's in a turnkey solution... sortof...
- download it here
http://wotho.ethz.ch/tk4-/tk4-_v1.00.zip - Extract and launch it
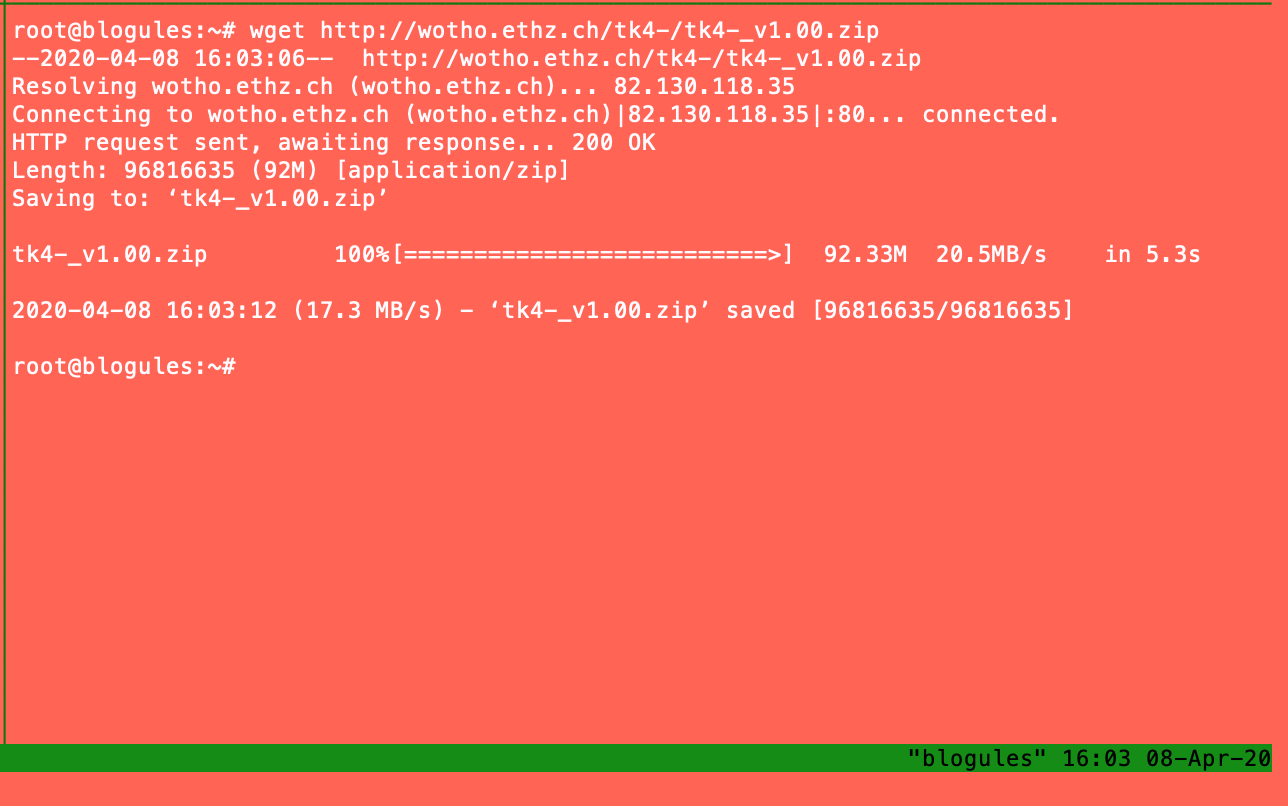
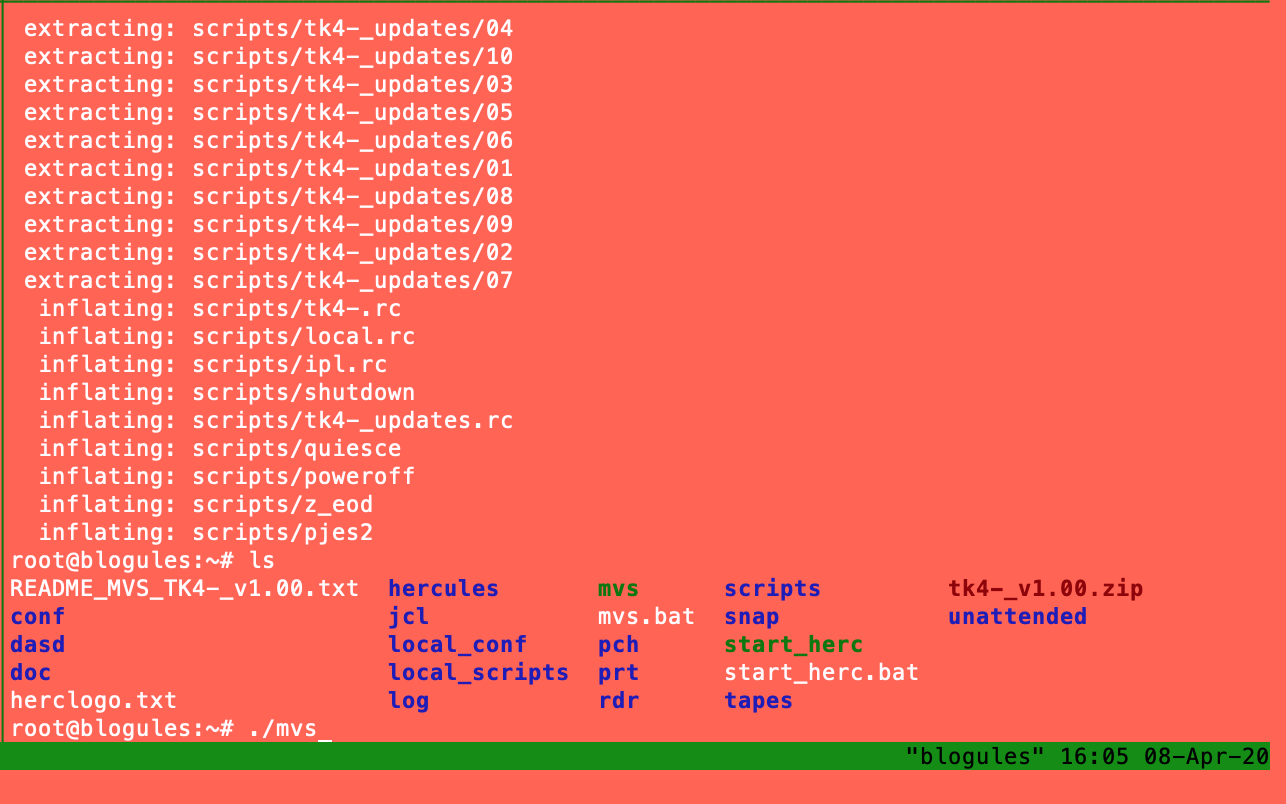
If everything goes well you should have this.
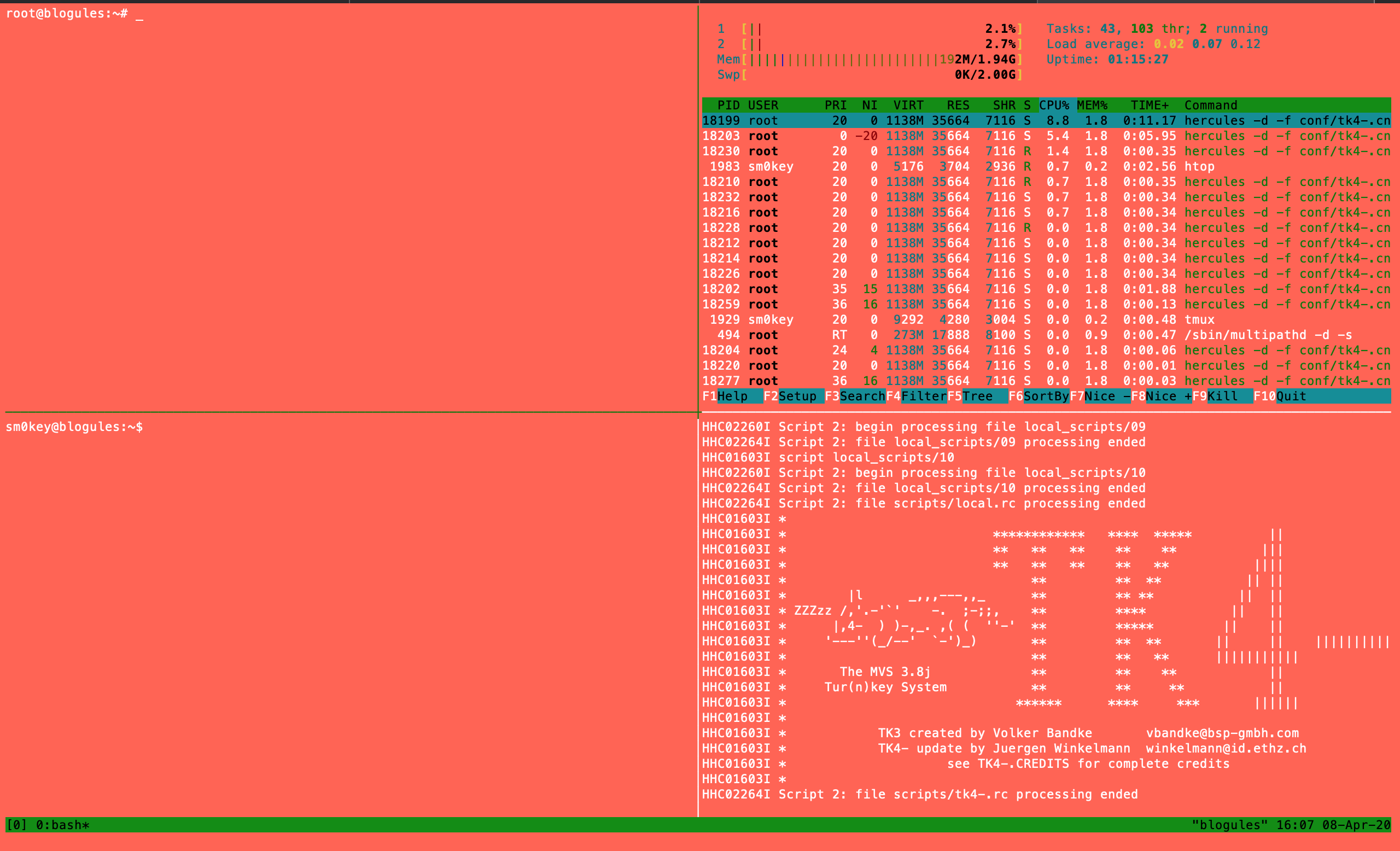
Smoke test the system
Now it is time to see if what we built actually works like a mainframe.
First step is make sure our host is listening on 3270.
netstat -tlunp
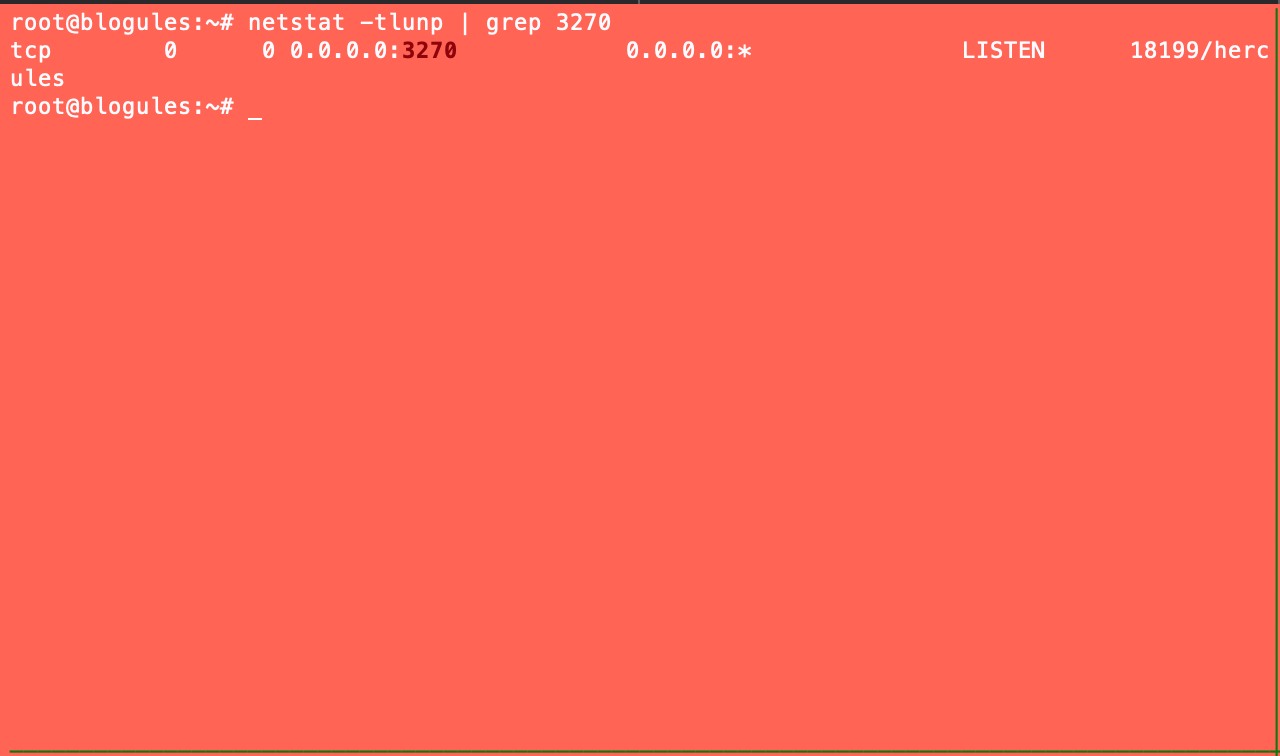
Next we will connect our emulator to our newly booted mainframe.

Pro-tip:
If you do not see the logon prompt, you will need to issue the clear screen command to your 3270 emulator. In c3270 the command sequence for that is ctrl + A C. Once you have done that you should have a logon prompt like this.
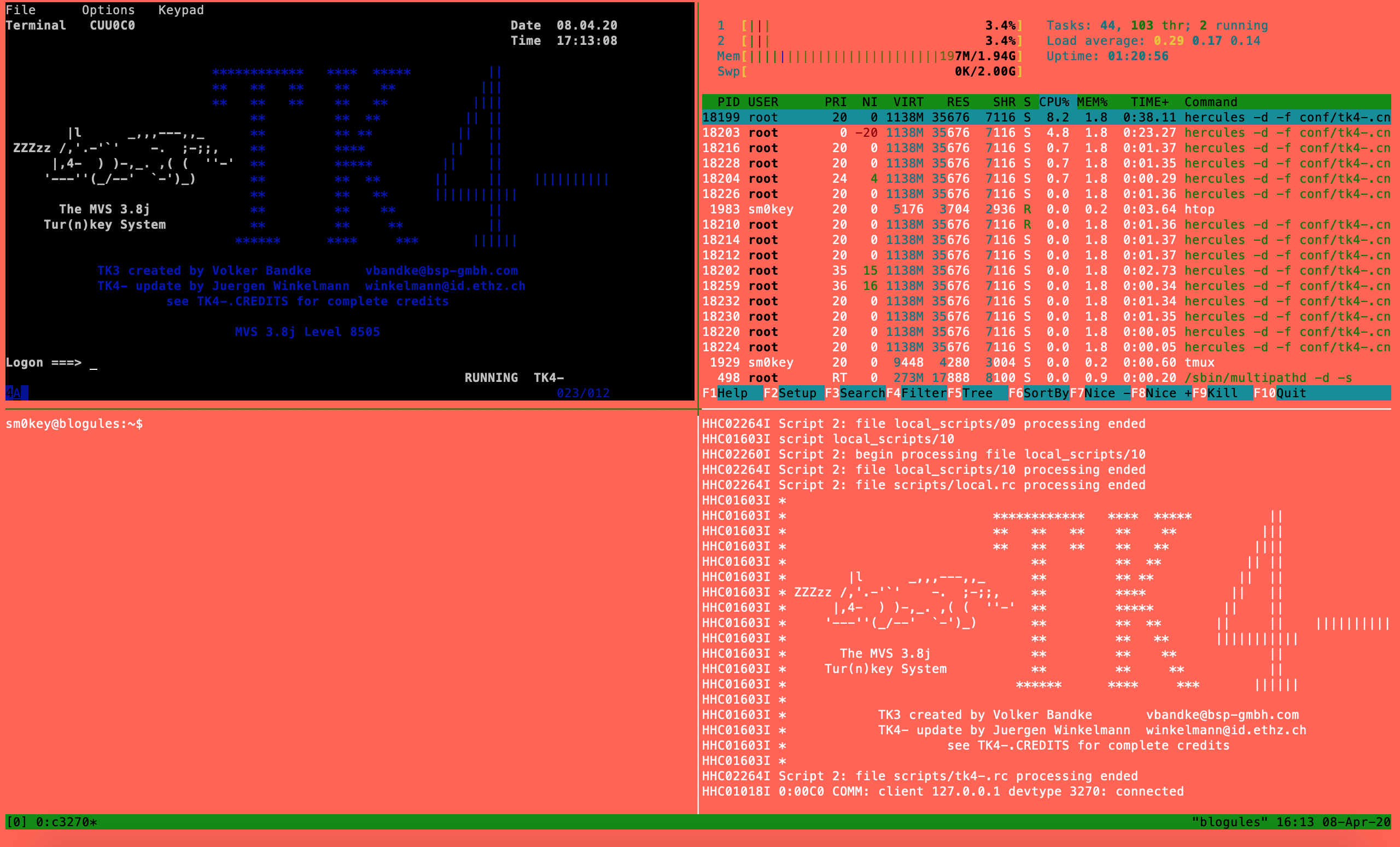
Now we will log in from two c3270 sessions and make sure we can use the TSO send command to message back and forth.
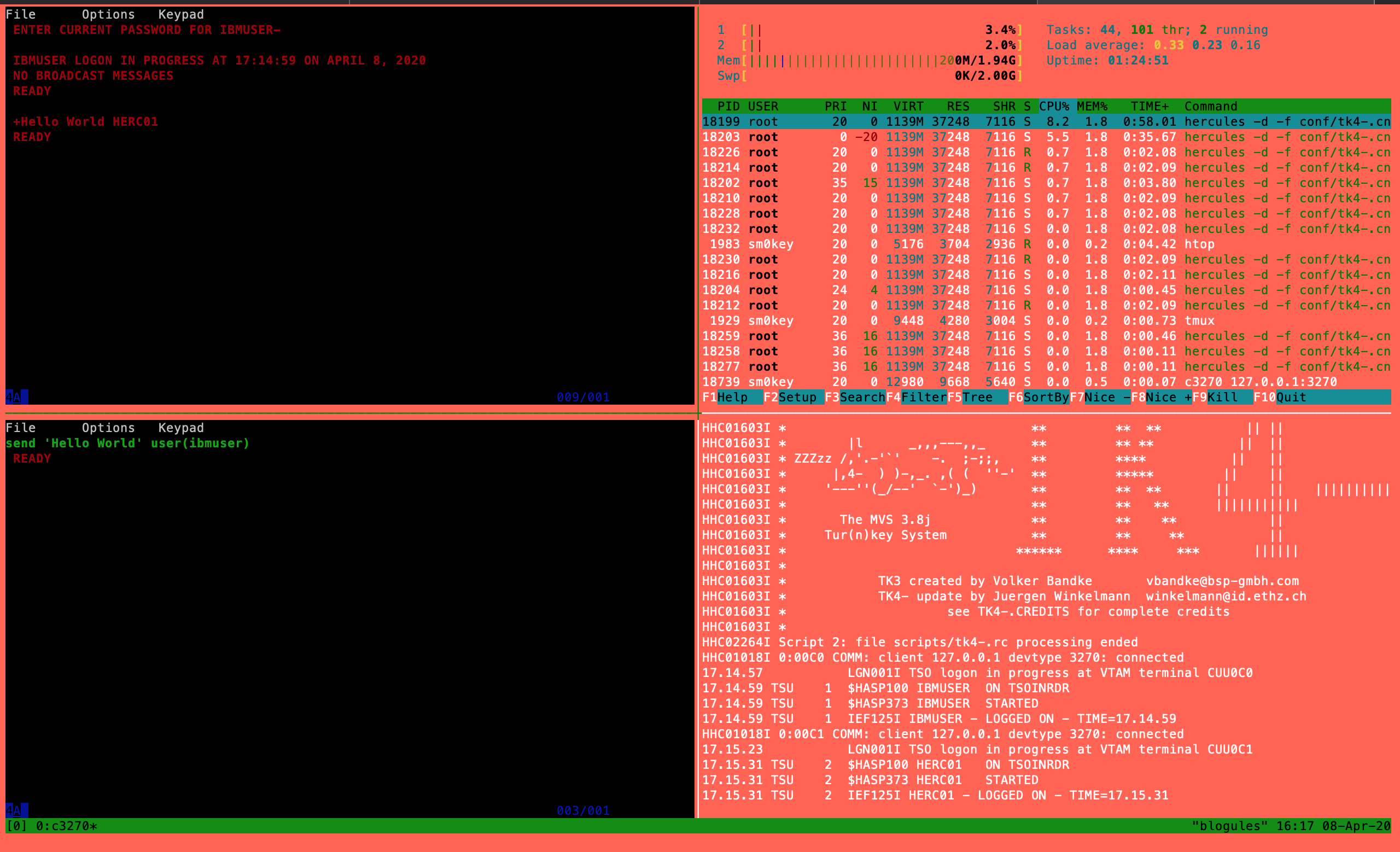
Lessons learned
After a minimal amount of research, and consulting with my magic 8 ball; I was able to make this boot and give me an environment in which to work. There are probably more secure, more elegent, more better, or whatever ways to do this. I wasn't able to find them, and this gets the job done.
Getting ahold of z/os to build from scratch is a pain in the ass.
Next steps:
Next up we will look at instrumenting a testing environment so we can abuse some vulnerable mainframe apps.